About Security Code Review
Identifying Security flaws in source code and how Play Framework can help
I had the opportunity to work some years ago in a startup from NYC offering (at the moment) automated security assessment, acting as a security rating platform. It was interesting to learn about the multiple sources of security flaws that a software product may have.
I was lately learning more about how to find security flaws in source code, from well known sources, like OSWAP and MITRE. Here are some of my notes (including some short guidance on how Play Framework may help to address them, in some cases), mostly based on what I did internally for my current job.
About OSWAP and MITRE
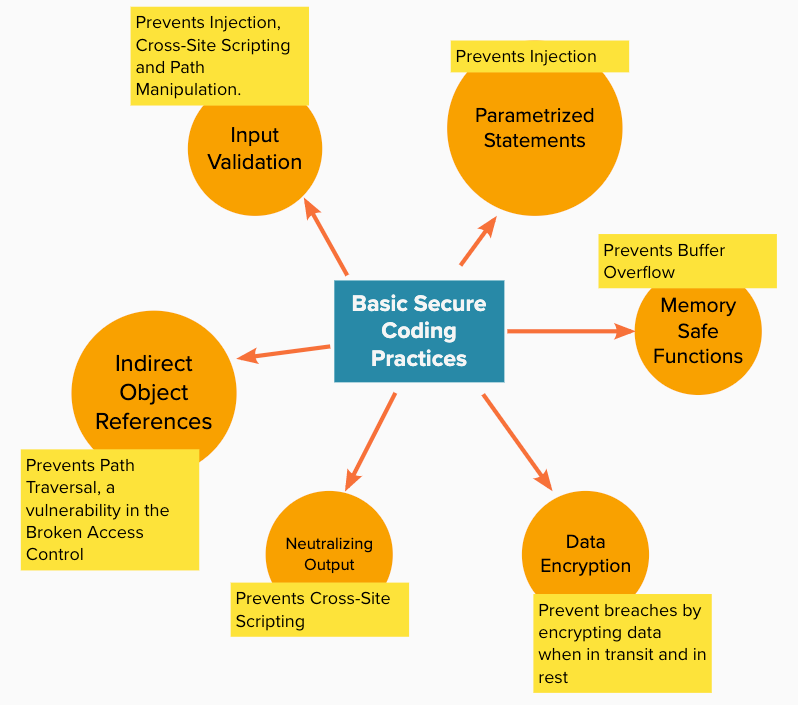
Both OSWAP and MITRE maintains a list of top security risks that are found in source code:
-
The CWE Top 25 from MITRE (CWE stands for Community Developed List of Common Weakness found in Software)
-
The Top 10 Web Application Security Risks from OSWAP
In general, the risks listed above can be addressed with the following coding practices:
 Made with https://app.mural.co/
Made with https://app.mural.co/
Top Web Application Security Risks
Here are the Top 10 Web Application Security Risks and how these can be addressed (just general approaches).
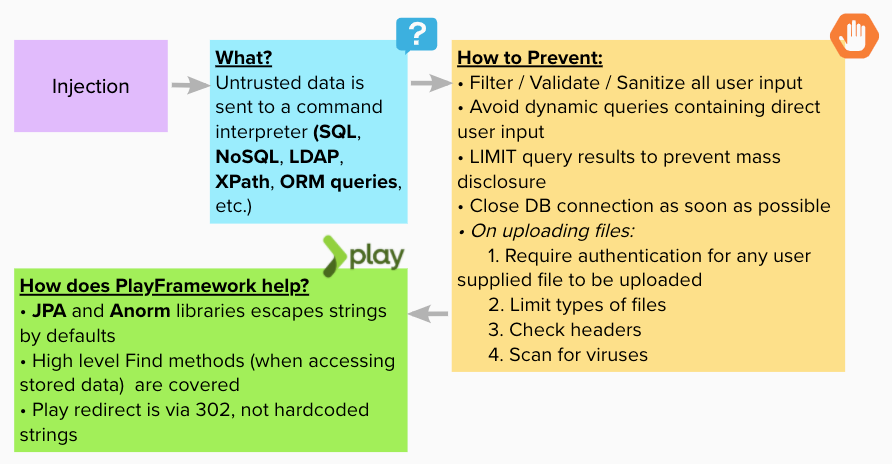
Injection
Happens when an attacker can send hostile data to an interpreter.
 Made with https://app.mural.co/
Made with https://app.mural.co/
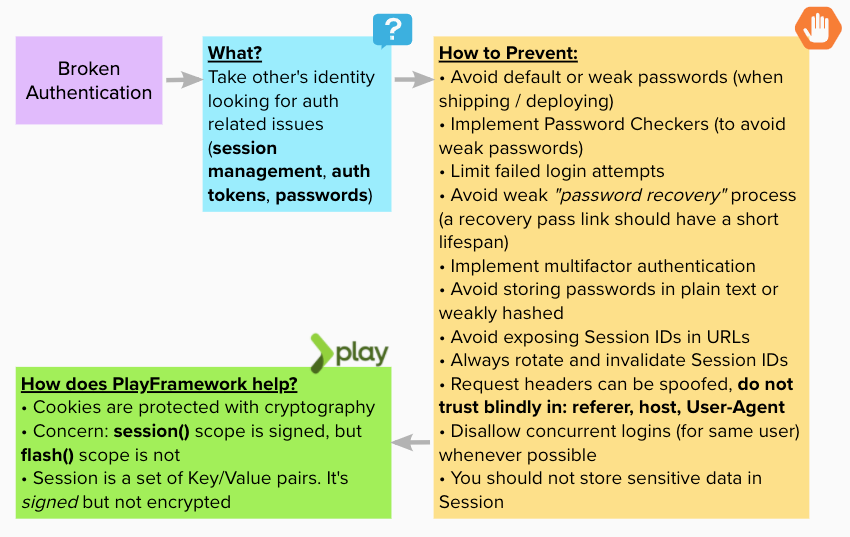
Broken Authentication
Issues in authentication and session management opens doors for attackers to gain access to valid sessions and credentials.
 Made with https://app.mural.co/
Made with https://app.mural.co/
Sensitive data Exposure
Happens when non encrypted data is in transport (maybe from server to browser, when attacker inspects the transport layer) or in rest (if attacker gain access to storage).
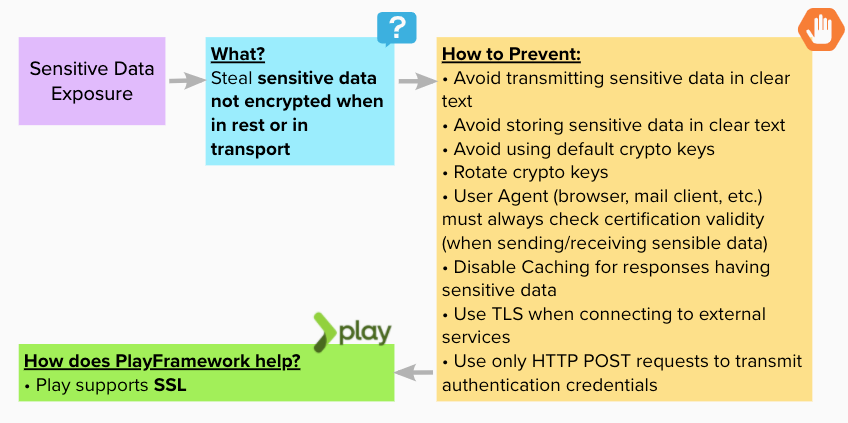 Made with https://app.mural.co/
Made with https://app.mural.co/
XML External Entities
Happens when old (or poorly) configured XML processors processes external (untrusted) XML entities.
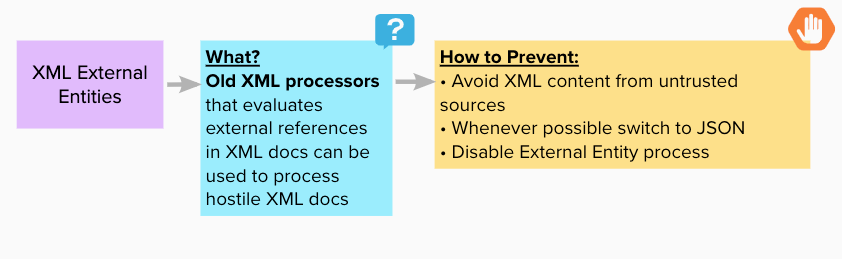 Made with https://app.mural.co/
Made with https://app.mural.co/
Broken Access Control
Happens when access control (role-based restrictions for authenticated users) are poorly configured.
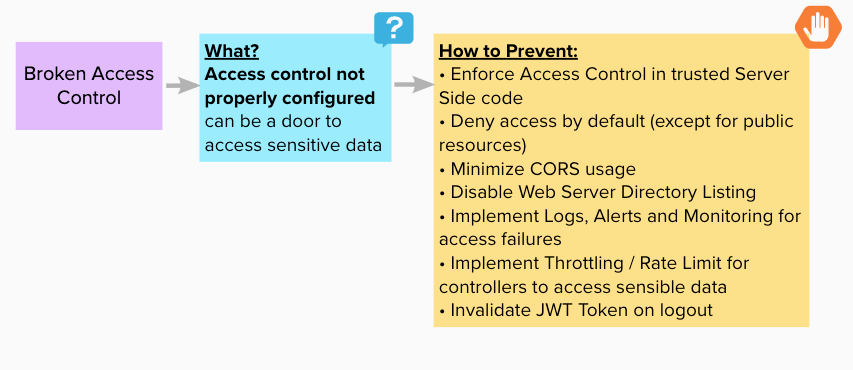 Made with https://app.mural.co/
Made with https://app.mural.co/
Security Misconfiguration
Happens when security configuration is not complete, done ah-hoc, or using defaults.
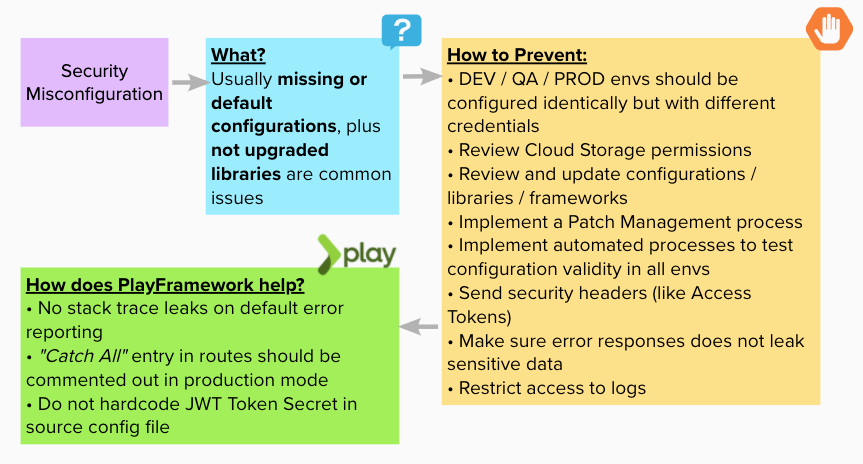 Made with https://app.mural.co/
Made with https://app.mural.co/
Cross Site Scripting (XSS)
Happens when a web page can include (untrusted) user supplied data can be used to render HTML/JS dynamically, allowing an attacker to act on behalf of the current user.
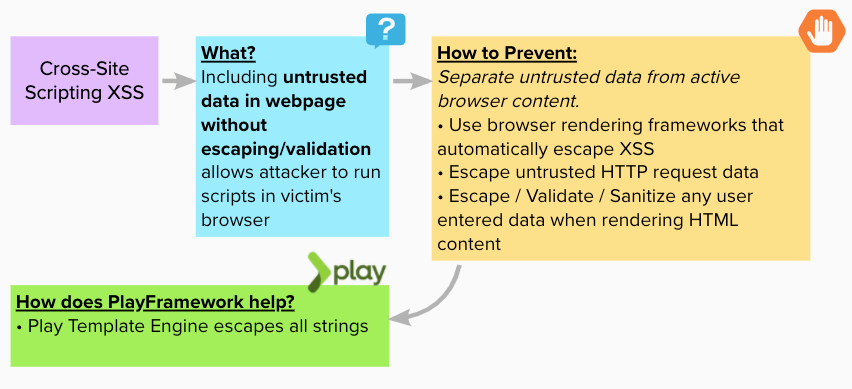 Made with https://app.mural.co/
Made with https://app.mural.co/
Insecure Deserialization
Happens when untrusted serialized data is sent to be deserialized in a secure context.
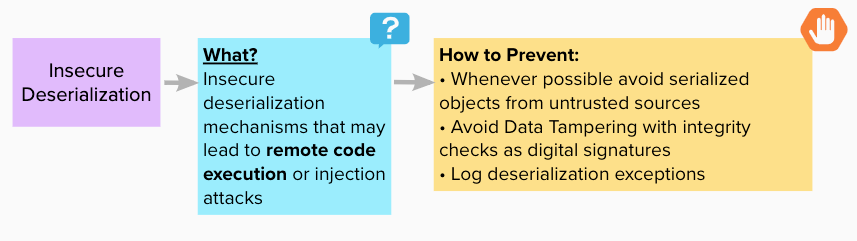 Made with https://app.mural.co/
Made with https://app.mural.co/
Using components with Known Vulnerabilities
Happens when libraries and/or frameworks with known vulnerabilities are not upgraded or replaced, allowing attackers to gain access taking advantages of these vulnerabilities.
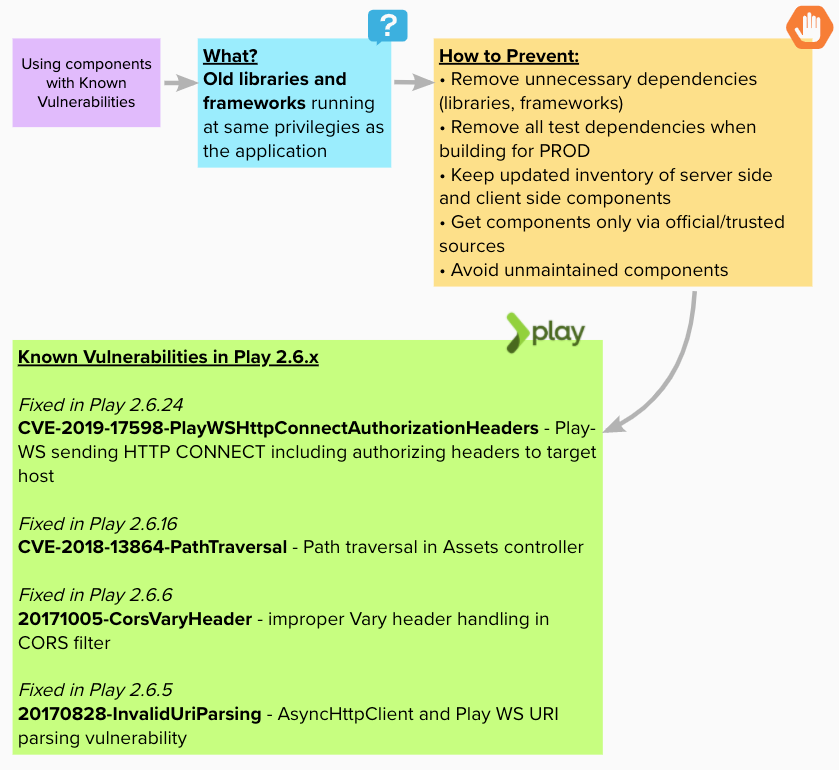 Made with https://app.mural.co/
Made with https://app.mural.co/
Insufficient Logging or Monitoring
Happens when Alerts / Logs / Monitoring not properly configured hides attacker actions on a compromised system.
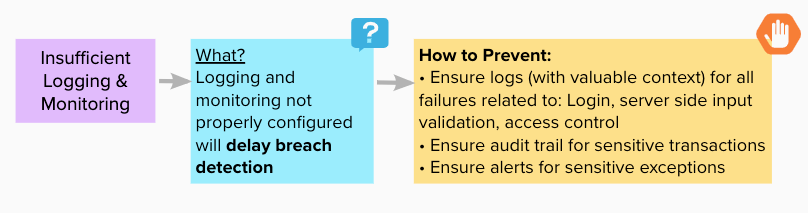 Made with https://app.mural.co/
Made with https://app.mural.co/